| Quantity | Price per item | Discount |
| 5 items | $170 | 5% off |
| 15 items | $152 | 15% off |
| 25 items | $139 | 22% off |
| 35 items | $128 | 28% off |
| 70 items | $115 | 36% off |
| 100 items | $110 | 39% off |
Delivery: Electronic/E-mail delivery
Mfg.Part:
Covers: 1 Server for 1 year (1 licenses minimum)
Contact us for a Trial!
[tab name='Overview']
Product Description:
[tab name='Key Benefits']
From protection to detection and response, Malwarebytes Endpoint Detection and Response for Servers safeguards an organization’s most valuable data. Built for organizations of all sizes that value efficiency, Malwarebytes Endpoint Detection and Response for Servers is designed from the ground up integrating and communicating across the detection funnel—all from a single agent and management console—to uniquely allow organizations to manage server security with speed, scale, and ease.
[tab name='Features']
Now, it’s easy to halt malware from spreading if a server is attacked. Malwarebytes Endpoint Detection and Response for Servers maximizes IT response capabilities, drawing from three modes of device isolation:
3. Sever isolation allows administrators to lock out the machine while the IT staff manages triage. In addition, the server isolation can be leveraged to prevent insider threats.
[tab name='Technical Specs']
| Systems Requirements: Included Components Malwarebytes cloud platform Malwarebytes Endpoint Protection (persistent Windows agent) Email and phone support Hardware Requirements Windows CPU: 1 GHz RAM: 1 GB (clients); 2 GB (servers)Disk space: 100 MB (program + logs) Active Internet connection |
Supported Operating Systems Windows 10® (32-bit, 64-bit) Windows 8.1® (32-bit, 64-bit) Windows 8® (32-bit, 64-bit) Windows 7® (32-bit, 64-bit) Windows Vista® (32-bit, 64-bit) Windows XP® with SP3 (32-bit only) Windows Server 2016® (32-bit, 64-bit) Windows Server 2012/2012R2® (32-bit, 64-bit) Windows Small Business Server 2011 Windows Server 2008/2008R2® (32-bit, 64-bit) |
Windows Server 2003® (32-bit only)
Please note that Windows servers using the Server Core installation process are specifically excluded. Windows Action Center integration not supported for Windows Server operating systems |
[tab name='Misc Info']
Disclaimer: Information may not be accurate or may change at any time. Access Scanning is just a re-seller, manufacturer owns rights and trademarks of software. Description was provided by manufacturer.

Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcor.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcor.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis.
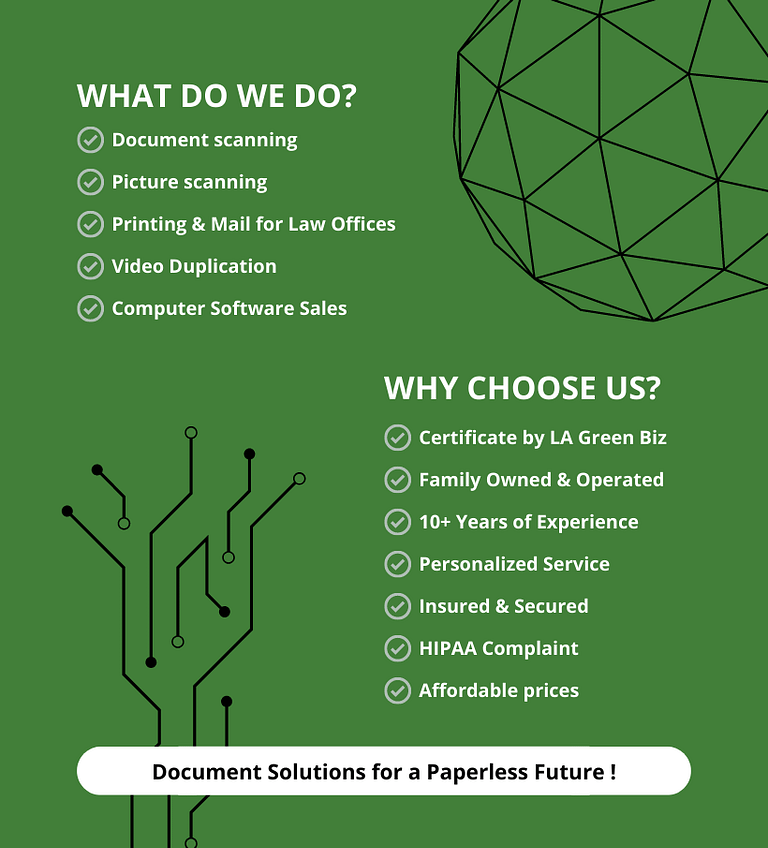
A privately family owned business located in Encino, CA. All work is supervised by the owners, leaving zero margin of errors by using innovative and highly secure equipment that delivers quality and accuracy. Working with a wide range of hard copy documents Access Scanning offers expert integration and utilization of information management systems. Our proven solutions are designed to provide clients with high quality, efficiency and accuracy; ensuring customer satisfaction.
Total Document Security including HIPAA Certification on top of the personalized business-specific scanning solutions tailored to your business
Personalized business-specific scanning solutions tailored to your business needs, with 100s of happy customers in all industries: lawyers, doctors, governments, universities and more.
Access Scanning is Certified by Los Angeles Green Business GreenBizLA.org
Multiple solutions for every business needs. Legal, Medical, Insurance, Goverment and more.
Complete projects with high standards of readability and professionalism
HIPAA compliant process. We at Access Scanning understand how important your documents are for you.
From industrial scanners to intelligent software, we are on top of the line of our industry!
Understanding your requirements is important, but applying your requirements to your project is crucial.
This place is great. Nice building, they also offer Notary services, quiet, quick and professional. I got my documents scanned right away and they were so accommodating because I did not have an appointment. And had I known they offer notary services I would've gotten that done there too and then done the scan. One stop shopping. I paid a low price I was there for a short amount of time and I really like the people that work there. Go for it!
We have been using Access Scanning at our law firm for our daily mail scanning about a year now and we are very pleased with their services. We receive thousands of documents a week and their turnaround time is quick and efficient. Javier and Lia are excellent at communicating any issues and working to resolve them with you. Since using their services our document processing time has decreased significantly allowing us more time to focus on our clients and resolve their cases quickly. I would recommend their services.
I talked to Javier a month ago before I head back to the US and clean up my old house with a box of important documents (Tax, legal, certificates etc.) and valuables pictures that I can’t bring back to Asia and
because Javier has been very responsive to my request. I even trusted them enough to mail the box over before I flew out in a rush. I felt very secure to mail to them to take care the rest of it, everything turned out perfectly high quality in a very reasonable price Javier quoted to me. I am highly recommend this scanning service to anyone who needs to clean out their office piling up with papers and documents.
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
Sign up to our Newsletter!
About Us
A privately family owned business located in Encino, CA. All work is supervised by the owners, leaving zero margin of errors by using innovative and highly secure equipment that delivers quality and accuracy.
Contact
Office
+1-818-429-5069
Text
+1-818-666-3969
16001 Ventura Blvd Suite 115 Encino, CA 91436
Document Solutions for a Paperless Feature!
© 2024 Access Scanning Document Services, LLC/Access Scanning Software